
In a complicated mess, a current Microsoft Protector upgrade presented a brand-new security function called ‘Kernel-mode Hardware-enforced Stack Defense,’ while getting rid of the LSA security function. Sadly, Microsoft has actually not offered any documents on this modification, resulting in more concerns than responses.
Regional Security Authority Defense, aka LSA Defense, is a security function that secures delicate info, like qualifications, from being taken by obstructing untrusted code from being injected into the LSASS procedure and LSASS procedure memory discarding.
Windows users can make it possible for LSA Defense in the Windows Security > > Gadget Security > > Core Seclusion settings page for CPUs that support virtualization.
Nevertheless, for the previous couple of weeks, Windows 11 users have actually grumbled that they can not make it possible for the Regional Security Authority Defense security function in the Windows Security ‘Core Seclusion’ settings.
When trying to do so, Windows triggers users to reboot the computer system to make it possible for the function, however on reboot, it would not be made it possible for, and Windows would as soon as again show a reboot timely.
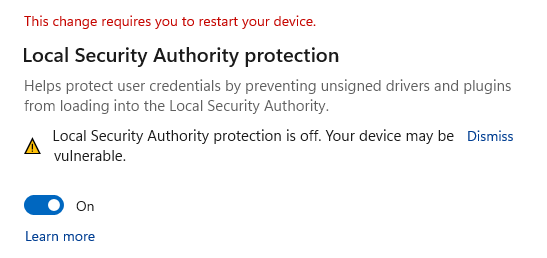
Microsoft later on stated that if you had actually made it possible for LSA Defense and rebooted your gadget a minimum of as soon as, you might neglect these cautions.
A workaround was likewise offered to examine if LSA Defense is made it possible for and how to set up 2 Computer system registry secrets to disable the caution.
Microsoft Protector upgrade develops confusion
A current Microsoft Protector upgrade has actually made this function a lot more complicated, as after it is set up, the LSA Defense function is eliminated and changed by a brand-new function called Kernel-mode Hardware-enforced Stack Defense.
Kernel-mode Hardware-enforced Stack Defense is a security function that tries to avoid ROP (Return Oriented Programs) based control circulation attacks that might cause code execution.
” For code running in kernel mode, the CPU verifies asked for return addresses with a 2nd copy of the address kept in the shadow stack to avoid enemies from replacing an address that runs harmful code rather,” describes the Windows Kernel-mode Hardware-enforced Stack Defense setting.
” Keep in mind that not all motorists work with this security function.”
Nevertheless, to utilize this function, a Windows gadget need to be utilizing Intel Tiger Lake CPUs or AMD Zen3 CPUs and later on. For that reason, Windows will just show this brand-new setting if the gadget has actually the needed hardware.
Like Memory Stability, when allowing Kernel-mode Hardware-enforced Stack Defense, Windows will make sure that no incompatible motorists are packed in Windows. If there are, the Stack Defense function will not make it possible for, and Windows will show a list of incompatible motorists.
Windows 11 users now report seeing Windows security alerts that the brand-new function is handicapped due to clashing motorists.
” Kernel-mode Hardware-enforced Stack Defense is off. Your gadget might be susceptible,” checks out a caution in the Windows Security Center.
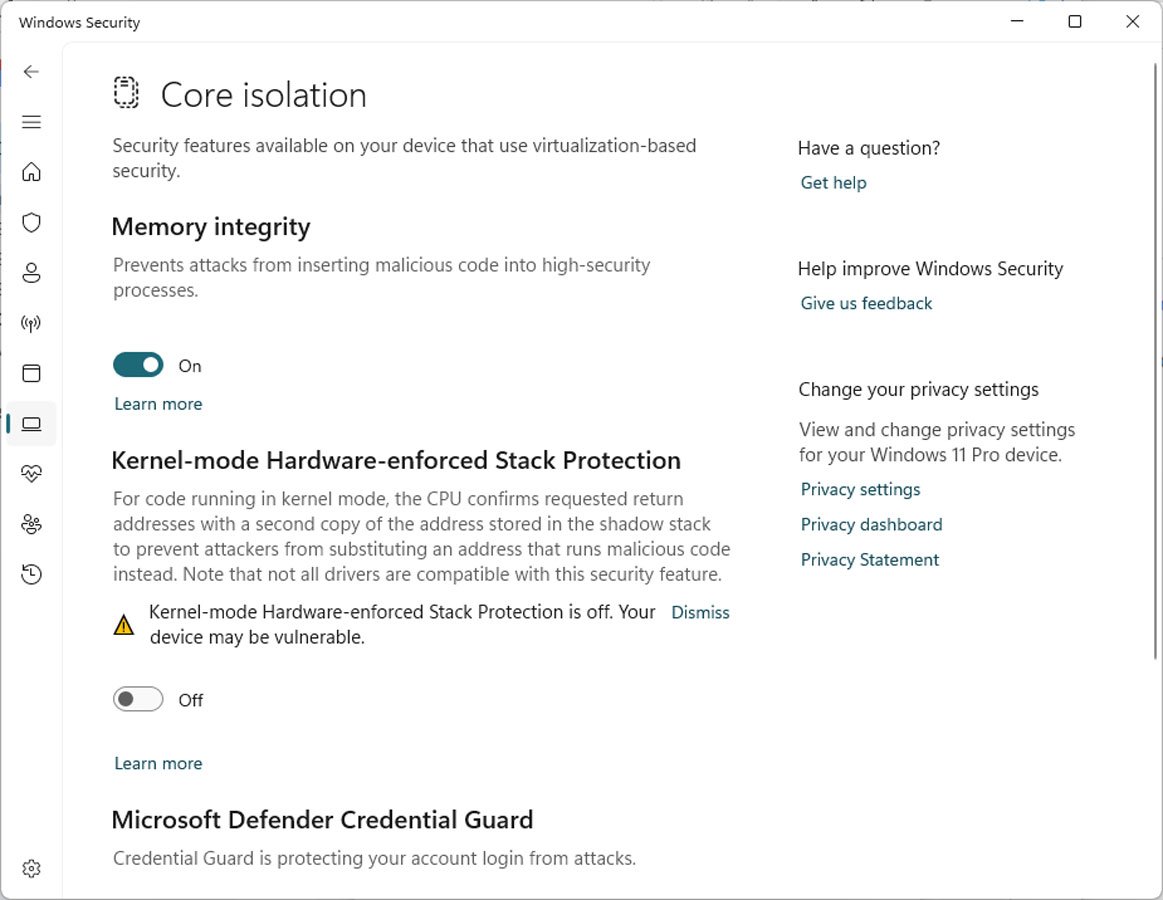
Source: BleepingComputer
Nevertheless, when they take a look at the list, it is empty, making it complicated how to make it possible for the function.
Even even worse, some conflicting video game anti-cheat motorists are not found as incompatible, and Kernel-mode Hardware-enforced Stack Defense is still made it possible for. These clashing motorists are triggering Windows to crash or for video games not to run when the security function is made it possible for and a video game is released.
Windows 11 users have actually reported these issues for PUBG, Valorant (Riot Lead), Bloodhunt, Fate 2, Genshin Effect, Phantasy Star Online 2 (Video Game Guard) and Dayz
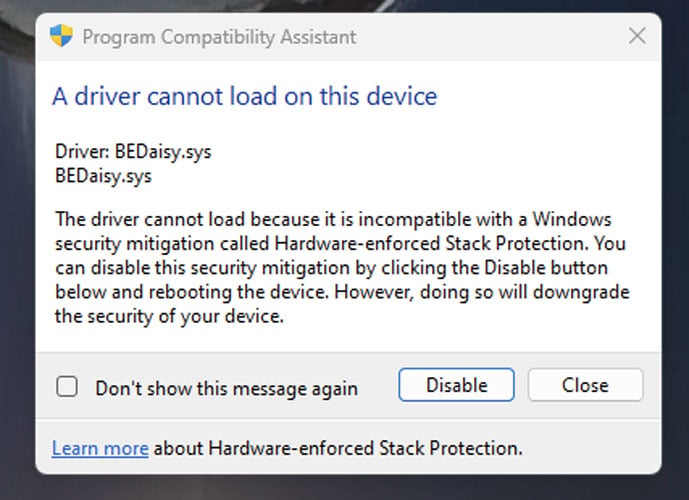
Source: Reddit
What occurred to LSA Defense?
Much more discouraging is that Windows 11 users can no longer make it possible for LSA Defense, which did not need more recent CPUs, from the Windows Security settings.
It’s not even clear if LSA security is bundled into the Kernel-mode Hardware-enforced Stack Defense or has actually been eliminated from the Windows Setting user interface completely, needing users to allow it by hand by means of the Computer system registry.
Moreover, there has actually been no notification from Microsoft about the switching of these security functions or about Kernel-mode Hardware-enforced Stack Defense being included aside from the short description discovered in Windows Security and the spread documents [1, 2, 3] on the Stack Defense function.
BleepingComputer asked Microsoft about the brand-new Stack Defense function if LSA Defense is now bundled within it, and the disputes individuals are having.
This short article will be upgraded with any actions we get.