Throughout architecture assessments, we generally determine technical-debt problems within a single system or task. Nevertheless, the effect of technical financial obligation typically reaches beyond the scope of a single system or task. In our work, we describe this type of technical financial obligation as business technical financial obligation Like all technical financial obligation, business technical financial obligation includes options profitable in the short-term, however typically bothersome over the long term. Overlooking business technical financial obligation can have substantial repercussions, so designers must look out for it, and they must not let it get ignored or neglected when they discover it. In this post, I offer examples of business technical financial obligation (and the danger it represents) drawn from real-world jobs.
As architecture critics, we have the special chance to see architectural dangers from more of a business viewpoint (instead of project-level), especially if we are taking part in assessments for a portfolio of jobs. Over the previous a number of years, the SEI has actually leveraged SEI technical-debt research study to institutionalise technical-debt practices at a company with a big portfolio of systems valued at over $100 million. This company has a portfolio of more than 2 lots service applications and follows a decentralized IT governance design. The examples in this post originated from our work as architecture critics on these jobs.
To make business technical financial obligation more concrete to readers, I offer 3 examples of business technical financial obligation products and repercussions. In a future post, I will enter into higher information about recording and remediating business technical financial obligation.
Example 1: A Breakable System-Integration Service
In this example (Figure 1), task requirements required exchanging information in between Applications A and B. The task groups made an architectural choice to utilize a shared database schema as the data-exchange system. This technique was interesting the groups at the time considering that it was simple to carry out, however later on it ended up being obvious that this service was fragile. In specific, when Group A made an independent modification to shared schema without collaborating with Group B, Application B needed to likewise make modifications to accommodate and vice versa.
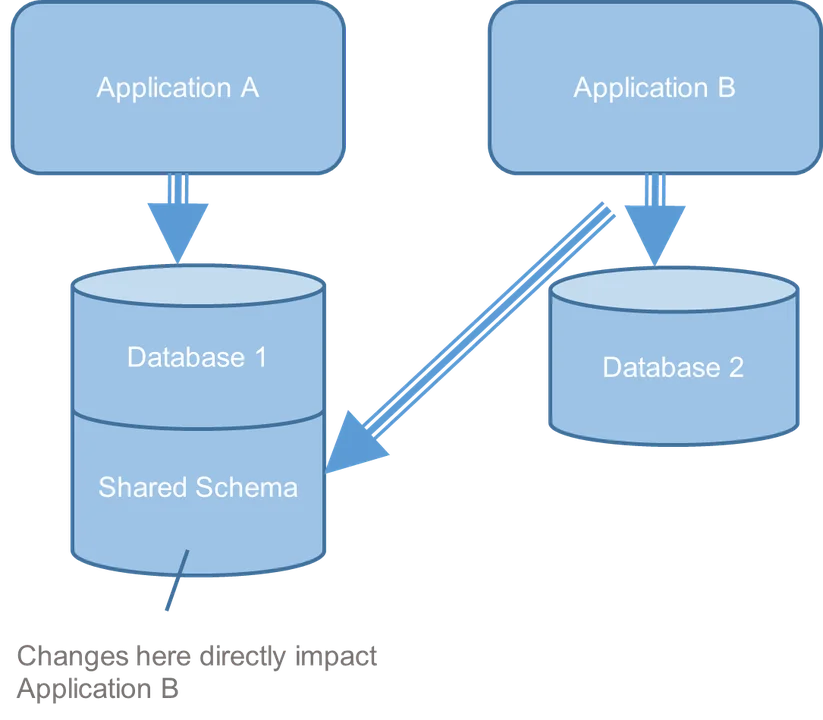
Figure 1: A Breakable System-Integration Service.
The groups created a workaround that made matters worse. The designers copied information in their regional environments to prevent altering the schema. The groups produced extract, change, load (ETL) tasks to keep information integrated that were undependable. When an ETL task stopped working, information was left in an irregular state. For instance, after failures, users would get various historic inquiry actions from Application A and Application B. Task function shipment likewise slowed since schema modifications needed lengthy analysis.
Both groups were pleased with the shared schema– a minimum of in the short-term. Nevertheless, from our architecture examination, which provides us an external and enterprise-level viewpoint, we might see that the unfavorable repercussions of this service were most likely to increase gradually as performance grew. For this factor, we advised changing the fragile shared-schema service with an application programs user interface (API) for application information exchange.
The groups easily accepted the proposed technical service, however the company did not act to repair the problem at first for a number of factors. Initially, in this decentralized governance environment, neither group felt accountable for the refactoring work. Second, repairing a fragile combination service was not considered as a top priority to business. For that reason, the item owners would not designate task funds to the redesign effort. Although no action would be taken in the near term, we produced a technical financial obligation product— a composed description of the problem and repercussion. Recording the problem as a technical financial obligation product enabled the company to make it noticeable and deal with a longer-range technique to remodel the service. I will offer examples of these technical financial obligation products we produced in a future post.
Example 2: Heterogeneous Gain Access To and Authentication-Control Solutions
As architecture critics for this company, we evaluated a number of task architectures in which the groups were carrying out duplicative authentication and access-control ability. Duplicative abilities consisted of
- capability to keep function and authorization details
- administrative ability to include, alter, and erase user approvals
- safe token generation
- capability to set and impose access-control policies for software application services (API calls)
A typical gain access to and authentication ability was not supplied, so the specific groups executed this ability in a heterogeneous way. Figure 2 illustrates 3 various application designs we observed.
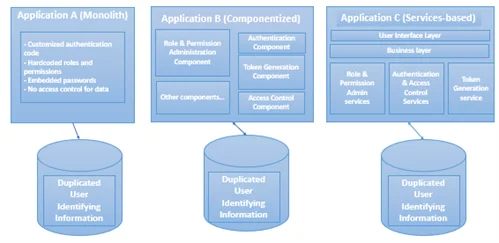
Figure 2: Heterogeneous Gain Access To and Authentication-Control Solutions.
- Application A is a tradition application established as a monolith, which is dated and has a number of downsides. For instance, the groups composed customized authentication code rather of utilizing safe, validated supplier elements. We likewise discovered that functions and authorization details were hard-coded, and less safe password qualifications were utilized rather of tokens for accreditation. Lastly, there was no application-level security check at the data-access layer.
- Application B was a more contemporary application with a component-based architectural design. In this application, there was separation of authentication and access-control ability into elements (e.g., functions and approvals administration, authentication, token generation, gain access to control). These elements were shareable by several customers.
- Application C had a service-oriented architecture. Solutions utilized were function and authorization administration, authentication, token generation, and gain access to control.
These heterogeneous authentication and access-control services eventually led to increased security and upkeep danger. For instance, without a typical administration module, user accounts were shut down (instead of erased), leaving the company available to impersonation attacks. In addition, altering user approvals included running error-prone handbook database scripts to upgrade a number of databases. Rather of saving user-identifying information in a single safe, reliable information source, that information was kept haphazardly in numerous functional task databases.
Once again, the task groups saw no issues with this scenario. When seen from the business viewpoint, nevertheless, the security and upkeep dangers were clear. To make this financial obligation noticeable, we produced a technical financial obligation product and dealt with the company to get it focused on. I will share the technical financial obligation product we produced for this example in the next post.
Example 3: Data-Warehouse Refresh Concern
Years back, the company bought developing a comprehensive information storage facility. Throughout architecture assessments, we discovered that a number of groups were not utilizing the data-warehouse reporting. Rather, they were running lots of intricate nighttime database tasks to copy historic information to their regional databases. We discovered that the source for this technique was a 48-hour lag in upgrading information to the information storage facility. Users were not pleased with seeing stagnant information, which left the information storage facility underutilized and included unneeded intricacy to the environment.
When once again, this scenario was great with the task groups. When evaluated from the business viewpoint, nevertheless, business and maintenance/cost dangers ended up being clear. For instance, the information copying triggered a surge in data-storage use. Complying to records-management requirements ended up being a headache after substantial copying made reliable information sources uncertain. Operations and upkeep personnel grumbled about hanging out tracking and upgrading the complex web of ETL synchronization tasks. As an outcome, we produced a technical financial obligation product recording the issue and advised a redesign to minimize data-warehouse lag time.
Looking Ahead
In this post, I explained 3 examples of business technical financial obligation. We showed, through example, the evasive nature of business technical financial obligation and the prospective effect untreated business technical financial obligation can have on a company. In our examples the effect of ETD products wasn’t felt at the technical level. Nevertheless, overlooking it led to multi-project or organization-wide dangers. These in turn increased expense, effectiveness, or security dangers for the company. I likewise talked about the designer’s function in using technical financial obligation practices to track and remediate technical financial obligation. In my next post, I will explain how we remediated these examples and how we directed groups to use technical financial obligation and governance practices to inspire action.