
Microsoft is presenting a brand-new Exchange Online security function that will immediately begin throttling and ultimately obstruct all e-mails sent out from ” constantly susceptible Exchange servers” 90 days after the admins are pinged to protect them.
As Redmond discusses, these are Exchange servers in on-premises or hybrid environments that run end-of-life software application or have not been covered versus recognized security bugs.
” Any Exchange server that has actually reached end of life (e.g., Exchange 2007, Exchange 2010, and quickly, Exchange 2013), or stays unpatched for recognized vulnerabilities,” The Exchange Group described.
” For instance, Exchange 2016 and Exchange 2019 servers that are substantially behind on security updates are thought about constantly susceptible.”
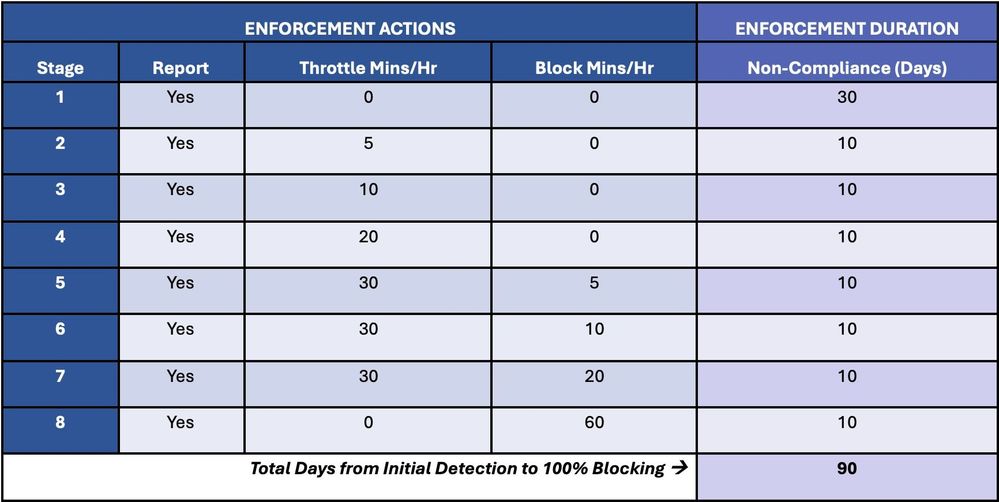
Microsoft states this brand-new Exchange Online “transport-based enforcement system” has 3 unique functions: reporting, throttling, and obstructing.
The brand-new system’s main objective is to assist Exchange admins recognize unpatched or unsupported on-prem Exchange servers, enabling them to update or spot them prior to they end up being security threats.
Nevertheless, it will likewise have the ability to throttle and ultimately obstruct e-mails from Exchange servers that have not been remediated prior to reaching Exchange Online mail boxes.
This brand-new enforcement system will just impact servers running Exchange Server 2007 utilizing OnPremises adapters to send out mail to enable great tuning prior to broadening to all Exchange variations, no matter how they link to Exchange Online, after tuning the
Redmond states it follows a progressive method created to slowly increase throttling and present e-mail obstructing till all e-mails sent out from susceptible servers are declined.
These enforcement actions are created to gradually intensify till the susceptible Exchange servers are remediated by elimination from service (for end-of-life variations) or covered (when it comes to releases still under assistance).
” Our objective is to assist clients protect their environment, anywhere they select to run Exchange,” stated The Exchange Group
” The enforcement system is created to alert admins about security threats in their environment, and to safeguard Exchange Online receivers from possibly destructive messages sent out from constantly susceptible Exchange servers.”
For some admins, guaranteeing that e-mails sent out from susceptible servers in their environment to Exchange Online mail boxes will not get immediately obstructed will likely be another “reward” that will contribute to their continuous effort to keep end-users secured versus possible attacks.
This statement follows a January call to action when Microsoft prompted clients to keep their on-prem Exchange servers updated by using the most recent supported Cumulative Update (CU) constantly to have them all set for inbound emergency situation security updates.
Microsoft likewise asked admins to use the most recent spots on Exchange servers as quickly as possible after releasing emergency situation out-of-band security updates to resolve ProxyLogon vulnerabilities made use of in attacks months prior to the main spots were launched.
More just recently, Microsoft covered another set of Exchange RCE bugs referred to as ProxyNotShell, 2 months after exploitation was initially spotted in the wild.
A Shodan search still reveals an enormous variety of Internet-exposed Exchange servers, with countless them waiting to be protected versus attacks targeting them with ProxyLogon and ProxyShell exploits, 2 of the most made use of vulnerabilities in 2021